Synology RT2600ac Security Features Review
TLDR; For $200 you get 802.11ac, Suricata, VPN capabilities in a single box.
Disclosure: This review is not supported/endorsed by Synology. This is my perspective on some security specific features not covered by other reviews.
Home networking for the InfoSec curious or veteran is a topic that seems to come up regularly. Some people take great pride in their pfSense, Ubiquity switched/multi AP environment, with multiple VLANs (for IOT device network segmentation) setups. These are great for the more experienced Network Engineer and/or InfoSec guy or gal, but what about the more casual (SOHO) power user? Or even someone on a tight budget?
Enter the Synology RT2600ac (yes, the NAS company) which has plenty of networking and security prowess hiding in a $200 dual core ARM based appliance. This has been my go to recommended gateway for co-workers and family who are tech savy but not ready to make the deep dive and expensive into prosumer home networking. This review focuses exclusively on the security features. If you want some reviews that go over the NAT performance, wireless range/speed, go check out the folks over at SmallNetBuilder.
The RT2600ac will be two years old at the time of this writing (February 2019). An important question to ask is how often are security vulnerabilities being addressed and how often does the router receive updates?
Synology seems to be on top of this as an December 2018 update fixed an RCE vulnerability (no authentication required!) and the list of release notes is impressive. WPA3 support was also added a few months ago.
Basic Configuration: automatic Updates, default configuration, and authentication.
Before moving onto the more advanced features, lets get the essentials of out of the way. For your non-technical or non security user, having an automatic update mechanism is essential. Thankfully you can choose between security updates and/or operating system (SRM) feature updates. This is similar to the Windows feature update settings in Windows 10. I have found the SRM releases to be quite stable. However, if you are going to be using this router in a mission critical setting . I wouldn’t fault anyone for going with security updates only.
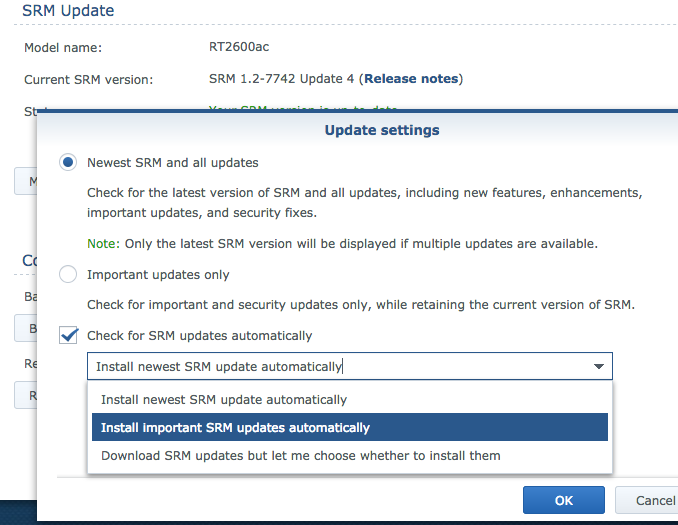
Gracefully, external access to the administrator page is only by “opt-in” (seriously though never do it!) and the router supports 2FA via the use of Time-based One Time Passwords (TOTP). This type of second factor is compatible with popular TOTP clients such as Google Authenticator, Authy, and others. This protection also extends to other apps in the SRM specifically Synology’s Web VPN.
Firewall and Geo-ip blocking
After you go through all of your configuration options and make sure everything works, you can start hardening your perimeter (also wise to turn off uPNP). Beginning with blocking several countries that you have no interest in exchanging traffic with and/or avoiding malicious infrastructure (botnets).
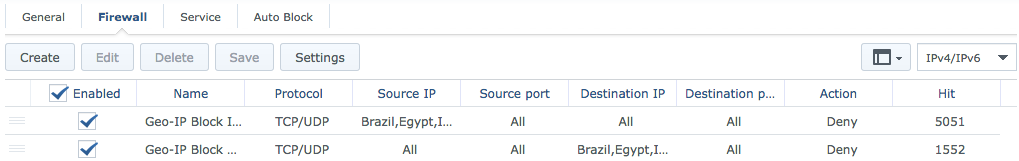
Each firewall rule listed above can have up to 15 countries in it. I just stick with 15, however you could go crazy and add 30, 45, 60 to cover even more territory. I wish that Synology would allow you to add as many countries as you want within one rule. The SRM UI is limited in the data it can display (more on that later).
Synology suricata
How in the heck does a $200 ARM based router run Suricata inline with little performance overhead? Well it took Synology almost two years to figure it out and after some tweaking it really does work! Prior to the November 2018 update, I was only pulling 30 Mbps from LAN <-> WAN on a family member’s 300 Mbps Comcast connection. Post update am seeing consistent 300 Mbps speeds. Really excellent for a 1.7 Ghz dual core ARM processor with only 512MB of RAM!
The downside is that managing Suricata from the GUI in its current state is less than ideal. The web server is fairly slow, there are several drill downs to find specific rules, and I see no place to write your own rules and/or download packet captures. I hacked away at it in the command line (Busybox shell) and could not get my custom rules to take effect in Synology’s version of Suricata (perhaps further testing will lead to another post).
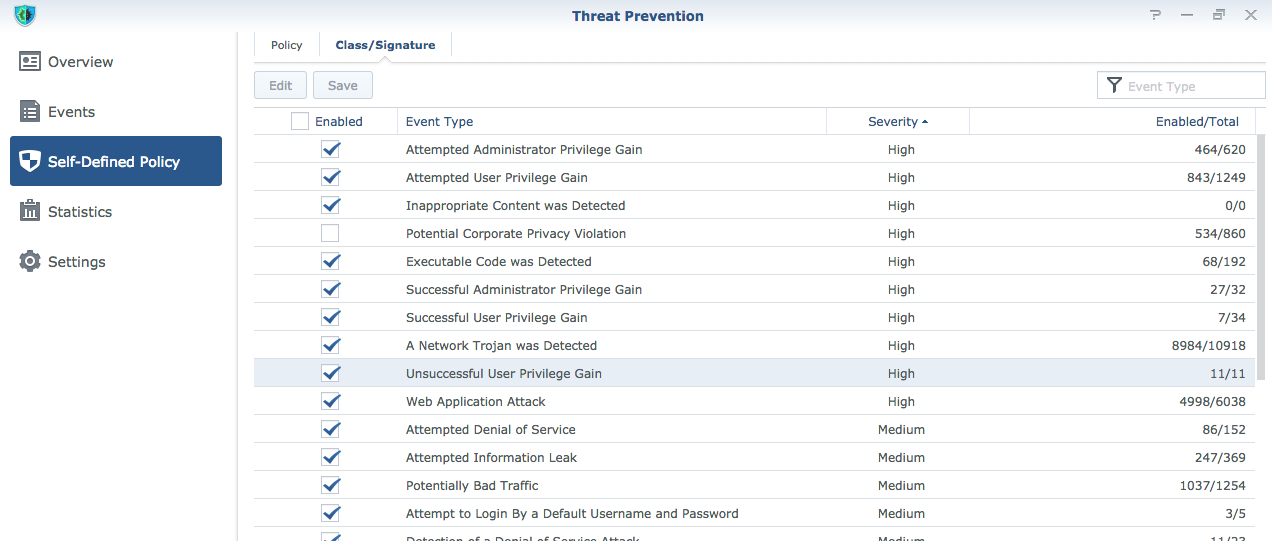
I should also mention the “Safe Browsing” application that launched in November 2018 as well. Its a competent parental control style app that uses some data from Google’s safe browsing project and an unknown source of “Threat Intelligence”. I have had a few false positives, but the lists are updated daily and I have not noticed a performance hit.
You may be better off using an DNS provider that does filtering such as OpenDNS (family shield/security) or Quad9 (security).
VPN
Synology’s SRM supports many of the most popular tunneling protocols such as SSTP, OpenVPN, IPSec, and PPTP VPN in addition to Synology’s proprietary apps.
SRM does create some other private subnets that allow you to segment VPN users from your primary systems and/or the guest network. I briefly used OpenVPN, which was easy to set up and came with great instructions for getting the necessary certificates/configs exported.
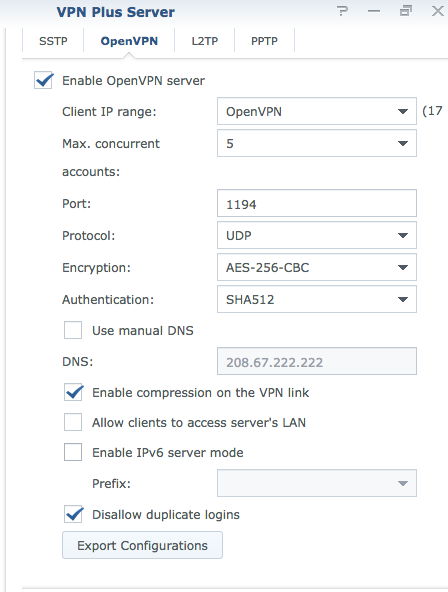
If you want to fly a little lower under the radar, you could run Synology’s SSL VPN over a more common port (443) and your traffic would look like a normal HTTPs connection to the rest of the world. The Synology app also supports 2FA which is another bonus.
PROS and CONs
Pros
- Extremely stable
- Incredible value at $200
- Regular security updates
- Late 2018 update allowed for Suricata to run with no appreciable performance hit.
- 2 Factor Authentication for admin access AND VPN
- Easy to use GUI
- Syslog support
Cons
- Slow to reboot (10 minutes) for a consumer router
- Odd UI bugs such LED on/off preferences not working or DNS settings greyed out for IPv6. (To their credit this was eventually fixed)
- Hardware limited, I would love to see what an extra $100 would allow for in terms of CPU and Memory (more cores? higher clocks? x86 base 1-2GB of RAM?)
- Easy to use GUI (Very few command line options)